Introduction
The Gentleman is a highly sophisticated ransomware group that emerged in mid-2025 and quickly established itself as a major threat actor. Their operations span at least 17 countries, targeting sectors such as energy, manufacturing, healthcare, insurance, technology, and telecommunications. Despite the diversity of victims, their attack methodology remains consistent: gain initial access, perform reconnaissance, disable defences, exfiltrate sensitive data, and encrypt critical systems. They have shown an interest to target a wide range of enterprise and large corporations including critical infrastructure. The ransomware gang also deploys README-GENTLEMEN.txt ransom notes with contact information and encrypts documents using the .7mtzhh file extension.
Tactical Overview
Their operations span at least 17 countries, targeting sectors such as energy, manufacturing, and healthcare. The group employs a double-extortion model, using strong encryption algorithms like XChaCha20 and Curve25519.
Victimology and Patterns
The Gentlemen ransomware group has been targeting organisations across multiple sectors, with a particular focus on the Asia-Pacific region. The manufacturing industry has been the hardest hit, followed closely by construction, healthcare, and insurance. The group’s attacks on essential services such as healthcare highlights its disregard for critical infrastructure and its potential public safety implications. Key target countries include Thailand and the United States, with a total of 17 countries affected.
Attack Patterns
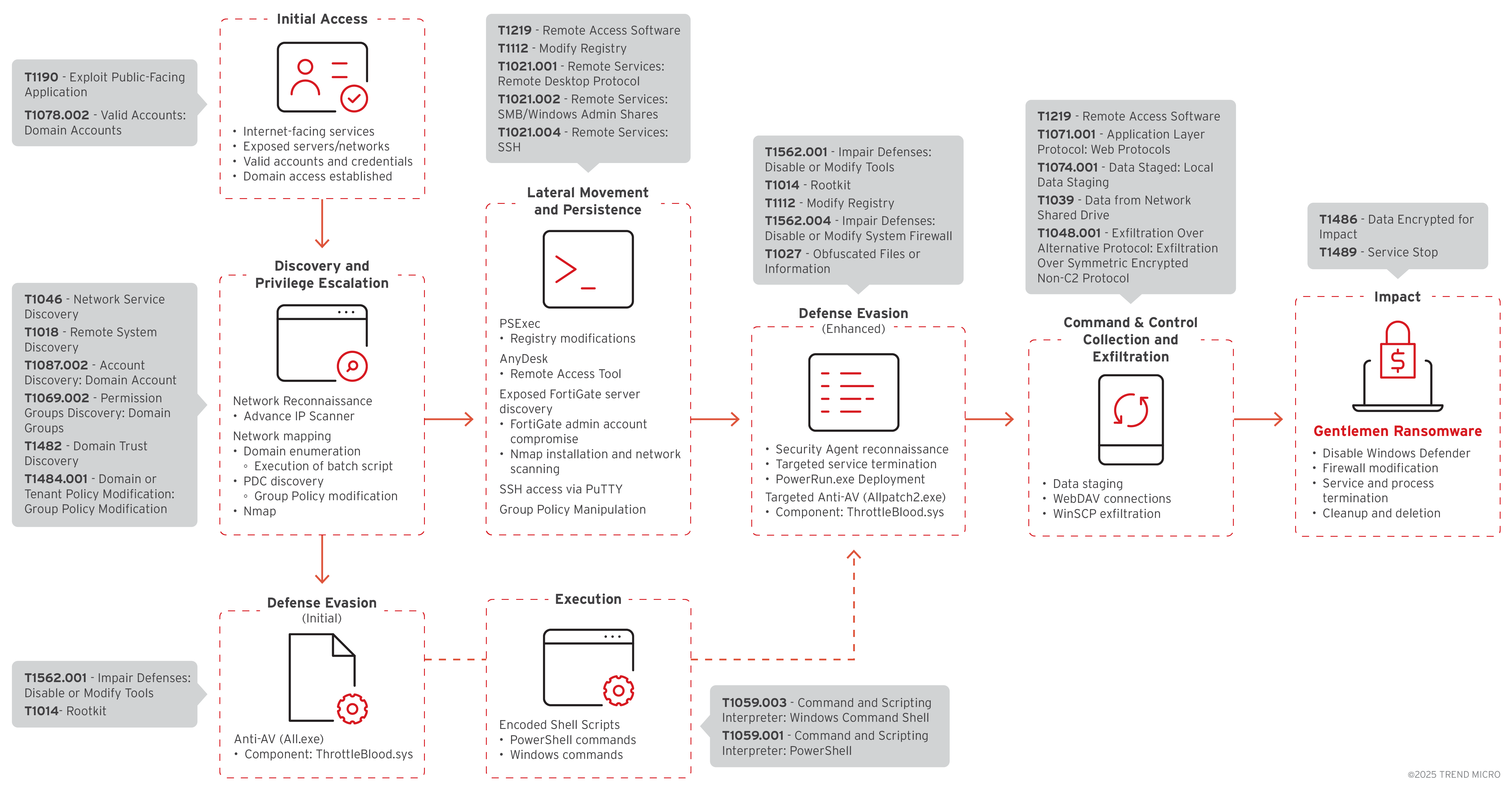
The group employs a double-extortion model, encrypting files while stealing sensitive data to pressure victims into paying ransom. Their malware is written in Go and uses strong encryption algorithms like XChaCha20 and Curve25519, making decryption without keys nearly impossible. They disable antivirus tools, delete logs and shadow copies, and manipulate Group Policy Objects for domain-wide compromise. Persistence and lateral movement are achieved through AnyDesk, PsExec, WinSCP, and PowerShell remoting, combined with legitimate signed drivers such as ThrottleBlood.sys to bypass kernel-level protections.
Exploitation of FortiGate VulnerabilitiesOne of their most notable tactics is exploiting FortiGate firewall and VPN vulnerabilities. These flaws allow attackers to bypass authentication or execute remote code, granting direct access to internal networks. Once inside, they conduct reconnaissance using tools like Advanced IP Scanner and escalate privileges to deploy ransomware across the environment. This method is particularly dangerous because FortiGate devices sit at the network perimeter, making them a high-value target for initial compromise. The pattern suggests The Gentlemen actively scans for unpatched FortiGate appliances, so timely patching and monitoring are critical defences.
IOCs
The Gentlemen’s leak site on the Tor network is professionally designed, featuring their logo, motto, victim pages, QR codes, and a public TOX ID for negotiations. As of late 2025, the group has listed over 60 victims, with earlier reports showing 32 victims by September and 48 by November. While victims span multiple industries, the attack chain is strikingly consistent: exploit perimeter vulnerabilities (often FortiGate), disable defences, exfiltrate data, and encrypt systems. This repeatable approach demonstrates a mature and well-organised operation.
IOCs are listed below:
1. Initial Access & Persistence
- Exploitation (T1190): Targets public-facing applications, specifically compromised FortiGate servers and admin accounts identified via Nmap.
- Credential Use (T1078.002): Utilization of compromised Domain Accounts.
- Remote Access (T1219): Installation of AnyDesk for persistent remote access and Command & Control (C2).
- Registry Persistence (T1112): Modifies registry keys to ensure tools remain active across reboots.
2. Discovery & Reconnaissance
- Network Mapping (T1046, T1018): Extensive use of Nmap and Advanced IP Scanner to map the internal environment.
- Account & Trust Enumeration (T1087.002, T1069.002, T1482):
- Batch scripts used to query domain accounts.
- Enumeration of domain groups.
- PowerShell used to identify the Primary Domain Controller (PDC) and domain trusts.
3. Defense Evasion & Execution
- Impair Defenses (T1562.001, T1562.004): Uses specialized "Anti-AV" tools and modifies firewall settings specifically to allow RDP access.
- BYOVD Attack (T1014): Deploys vulnerable drivers (Rootkit technique) to terminate security processes.
- Obfuscation (T1027): Executes Base64 encoded PowerShell commands to hide malicious intent.
- Scripting (T1059.001, T1059.003): Heavy reliance on
cmd.exeand PowerShell for deploying the final ransomware payload.
4. Lateral Movement & Escalation
- GPO Manipulation (T1484.001): Modifies Group Policy Objects to achieve domain-wide impact and privilege escalation.
- Lateral Tools:
- PSExec (T1021.002) for SMB/Admin share movement.
- RDP (T1021.001) (enabled via registry) for GUI-based movement.
- PuTTY (T1021.004) for SSH-based movement.
5. Collection, Exfiltration & Impact
- Staging (T1074.001): Data is gathered locally in
C:\ProgramData\data. - Network Shares (T1039): Uses WebDAV connections to harvest data from internal network shares.
- Exfiltration (T1048.001): Uses WinSCP to move data out via encrypted non-C2 protocols.
- Final Impact (T1486, T1489): Deployment of ransomware via the NETLOGON share and termination of remaining security services.
The Gentleman is a highly sophisticated ransomware group that emerged in mid-2025 and quickly established itself as a major threat actor. Surfacing in August of 2025, they are known for using compromised credentials and targeting Internet-exposed services to gain initial access to victims' networks.